Understanding Python 2 Security Risks and Vulnerabilities
Written on
Introduction to Python 2 End-of-Life
In January 2020, the Python Software Foundation made the decision to officially discontinue Python 2. They noted that while volunteers may still offer help for Python 2 software, their numbers will steadily decline over time. This blog post delves into the reasons behind this decision, the security ramifications, and the vulnerabilities that were found and exploited in Python 2.
Python 2.0 was first released on October 16, 2000, and since then, the Python Software Foundation has consistently released updates, introducing new features and significant enhancements. The introduction of Python 3.0 in 2006 was a pivotal moment, yet many users preferred the familiarity of Python 2, leading to continued development in both versions.
Despite the cessation of official support, a substantial number of commercial applications still rely on Python 2, and many organizations have no plans to transition to Python 3. It’s worth noting that a large portion of GitHub repositories and available packages are still based on Python 2. When was the last time you used pip3 instead of pip to install a package?
Currently, there are 85 documented vulnerabilities affecting both Python 2 and 3, detailed in a curated list. These vulnerabilities exist within the core Python framework and various packages. While many may not have public exploits, this situation can inadvertently benefit companies utilizing these vulnerable components.
This blog will focus on a specific vulnerability in Python 2 that can expose sensitive data and potentially bypass critical security checks.
Vulnerabilities in Python 2
Here, we will examine the vulnerabilities associated with the input() function in Python 2. This specific vulnerability is unique to Python 2.
Python 2 offered two methods for accepting user input: input() and raw_input(). The raw_input() function was eliminated in Python 3, with its functionality being integrated into input(). So, what happened to the input() function in Python 2?
To understand this, let's clarify the distinction between the two functions:
- input(): Accepts user input without altering its type.
- raw_input(): Takes user input and converts it to a string type unless instructed otherwise.
In the example below, I've created a simple Python program that collects user input, first using the input() function, followed by the raw_input() function.
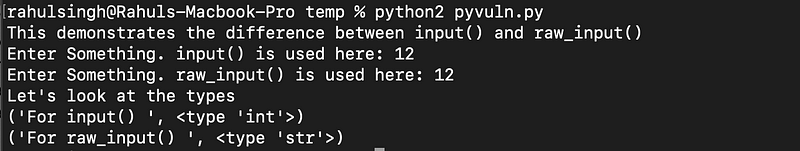
As illustrated, the raw_input() function converts the input into a string, while the input() function maintains the original data type. But how does this create a vulnerability?
By exploiting this flaw, a malicious individual can input a value that matches the name of a defined variable in the program. Consequently, the Python 2 interpreter may not recognize it as user input, which can facilitate authentication and other logic bypasses. Let’s explore this through a straightforward example.
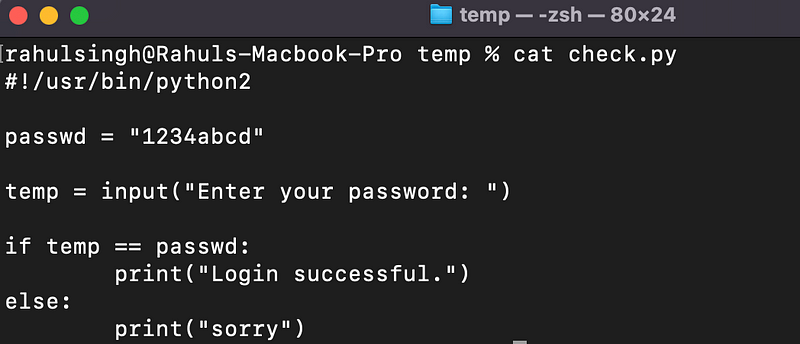
Example 1: Authentication Bypass
Imagine we have a Python script designed for admin login, which checks a user-supplied password against a hard-coded value. If the supplied password matches "1234abcd", the program will print "Login successful."
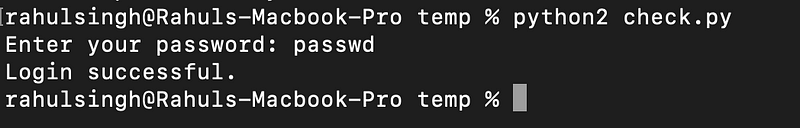
Everything seems secure until you realize that a user can log in without actually providing the correct password. If the user knows the variable name holding the password, they can input "passwd", and since only the string is being matched, they will gain access.
Example 2: Code Execution
Consider another simple Python program that takes user input and displays it on the screen using the input() function.
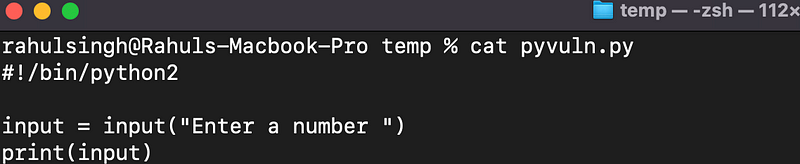
If a user enters "2+2", the input() function will execute this expression.
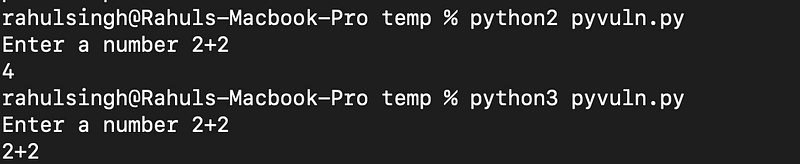
Note: This vulnerability does not exist in Python 3.
As you might expect, this could lead to serious risks, including denial of service (DoS) attacks if a user provides an excessively long string. For instance, if a malicious user imports the OS module, they could execute code on the server, resulting in Remote Code Execution. Below is a snippet illustrating this threat.
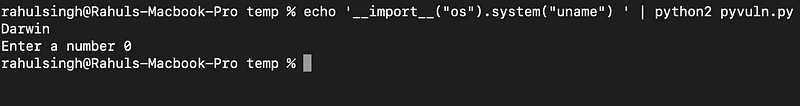
The snippet shows that the input function (in Python 2) not only accepts user input but also executes it.
Conclusion: The Urgency for Transition
These examples highlight just a few of the numerous vulnerabilities within the Python 2 programming language. Although there may not be public exploits available at present, the identification of these vulnerabilities suggests they could be exploited in the future. It is crucial to migrate to Python 3 to mitigate these risks. As long as organizations continue to rely on Python 2, attackers may exploit existing vulnerabilities, making it imperative to prioritize transition efforts.
The first video, "Python Coding Mistakes, Causes of Vulnerabilities and How to Solve It!" by Christopher Van Der Made, provides an overview of common pitfalls in Python coding that lead to vulnerabilities, along with solutions.
The second video, "What's Wrong with this Code? Vulnerable Python Code - Walkthrough and Fix," walks through examples of vulnerable Python code and demonstrates how to fix these issues.